zk-STARKs vs zk-SNARKs Decision Guide
Which Zero-Knowledge Proof System Is Right for Your Project?
Answer these key questions to get a tailored recommendation based on the article's analysis.
Project Requirements Assessment
Key Comparison
| Feature | zk-SNARKs | zk-STARKs |
|---|---|---|
| Proof Size | 188-1,500 bytes | 45KB-200KB |
| Gas Cost | 300k-500k gas | 1M-2M gas |
| Trusted Setup | Required | Not required |
| Quantum Resistance | Not resistant | Resistant |
| Developer Experience | More mature tools | Steeper learning curve |
Your Recommendation
When you hear about blockchain scaling solutions like Starknet or zkSync, you’re really hearing about two competing technologies: zk-SNARKs and zk-STARKs. Both promise to make blockchains faster, cheaper, and more private-but they’re built on totally different rules. Choosing between them isn’t just about tech specs. It’s about what kind of blockchain you’re building, who you’re building it for, and how long you expect it to last.
What Exactly Are zk-SNARKs and zk-STARKs?
At their core, both zk-SNARKs and zk-STARKs are zero-knowledge proofs. That means one party can prove they know something-like a secret password or a valid transaction-without actually showing what that thing is. Imagine proving you’re over 21 without showing your ID. That’s the magic.
zk-SNARKs, short for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, were the first to make this practical on blockchains. They debuted in 2012 and were first used in Zcash in 2016. Their big win? Tiny proof sizes-around 188 to 1,500 bytes. That’s smaller than a tweet. On Ethereum, verifying one takes about 300,000 to 500,000 gas, which keeps transaction fees low.
zk-STARKs, or Zero-Knowledge Scalable Transparent Arguments of Knowledge, came later in 2018. They’re bigger-proofs range from 45KB to 200KB-but they don’t need a trusted setup. That’s huge. And they’re built to resist quantum computers, something zk-SNARKs can’t promise.
The Trusted Setup Problem
This is where zk-SNARKs stumble. To work, they need a one-time setup ceremony where cryptographic parameters are generated. If even one person involved in that ceremony keeps a copy of the secret keys, they could forge proofs forever. No one would know.
Zcash’s original ceremony in 2016 had six participants across five countries. Each destroyed their part of the secret after contributing. It was messy, expensive, and required trust. Even though newer setups like the Powers of Tau ceremony (used by Ethereum’s zk-Rollups) have improved this-cutting setup time to under a day-the risk hasn’t vanished. Many developers still worry about it.
zk-STARKs skip this entirely. They use public randomness and hash functions. No secrets. No ceremonies. No trust needed. That’s why projects like StarkWare and Immutable X chose them. If you’re building something meant to last decades, this matters.
Speed, Size, and Gas Costs
Proof size is a big deal on Ethereum. Every byte you send to the chain costs gas. zk-SNARKs win here. A 200-byte proof? That’s cheap. zk-STARKs? 50,000 bytes or more. That means verification costs 1 to 2 million gas-3 to 5 times more than zk-SNARKs.
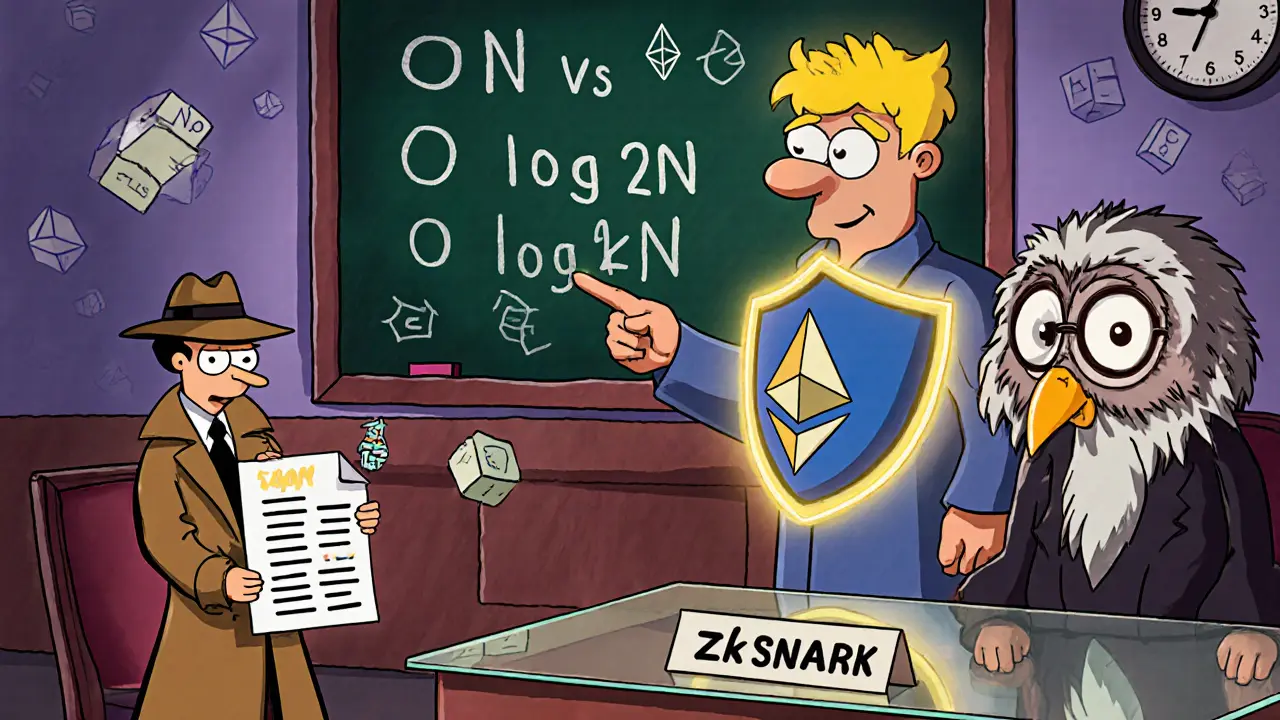
But here’s the twist: zk-STARKs get better as the computation gets bigger. Their verification time scales as O(log²N), meaning doubling the work doesn’t double the cost. zk-SNARKs scale as O(N). So if you’re verifying a million transactions at once-like a high-volume NFT marketplace-zk-STARKs become more efficient over time.
Verification speed also differs. zk-SNARKs verify in 1-10 milliseconds. zk-STARKs take 10-200 milliseconds. That’s fine for batch processing on layer 2s, but not ideal for apps needing instant responses.

Quantum Resistance: The Long Game
Quantum computers are coming. IBM’s roadmap points to machines powerful enough to break elliptic curve cryptography by 2030. That’s not science fiction-it’s engineering.
zk-SNARKs rely on ECC. If quantum computers arrive, all zk-SNARK-based systems become vulnerable. Someone could forge transactions, drain wallets, and nobody could stop them.
zk-STARKs use hash functions like SHA-256 or SHA-3. These are considered quantum-resistant. Even a powerful quantum computer can’t easily reverse them. That’s why Eli Ben-Sasson, the co-inventor of zk-STARKs, says they’re the only way to future-proof blockchain infrastructure.
If you’re building a financial system or long-term identity layer, this isn’t optional. It’s essential.
Developer Experience: Learning Curves and Tools
Getting started with zk-SNARKs isn’t easy, but it’s easier than zk-STARKs. Tools like Circom and SnarkJS have been around since 2017. There are hundreds of tutorials, GitHub repos, and Discord communities. Experienced developers can build their first zk-SNARK circuit in 4-6 weeks.
zk-STARKs? You need to learn Cairo, a new programming language designed specifically for STARKs. It’s not like Solidity. It’s more like writing assembly code with math constraints. StarkWare’s documentation is good, but it’s still half the size of zk-SNARK resources. Developers report spending 8-12 weeks to become productive.
GitHub stats show the difference: SnarkJS has over 4,200 stars. Starknet.js has 2,800. Open issues? SnarkJS has 1,100+. Starknet.js has 750+. More users, more bugs, more help. But the gap is closing fast.

Who’s Using What?
Right now, zk-SNARKs dominate. About 72% of live ZK projects use them. Zcash, Tornado Cash, and early versions of zkSync and Loopring all rely on zk-SNARKs. Why? Because they’re proven, cheaper, and easier to integrate.
But zk-STARKs are growing fast. Their market share is 28% and growing at 3.2x the rate of zk-SNARKs. Why? Because they’re better for scale.
Immutable X, a gaming platform handling millions of NFT trades, uses zk-STARKs. Their order book is too complex for zk-SNARKs. Polygon’s zkEVM uses zk-SNARKs for simple transfers but is testing STARKs for advanced logic. Starknet, the first fully decentralized zk-STARK chain, now has over 1,000 dApps.
Enterprises are split. Banks and regulated firms prefer zk-SNARKs because they’re easier to audit and comply with. Gaming and DeFi platforms pick zk-STARKs for speed and quantum safety.
The Future: Hybrid Systems Are Coming
Neither side is winning. The future isn’t zk-SNARKs OR zk-STARKs. It’s zk-SNARKs AND zk-STARKs.
Projects like Polygon Miden and Scroll are already blending both. They use zk-SNARKs for simple transactions and zk-STARKs for complex ones. Halo 2, a zk-SNARK variant without trusted setup, is gaining traction. It’s not perfect-it has larger proofs-but it removes the biggest flaw of traditional SNARKs.
StarkWare’s new DEEP-ALG optimization cut STARK proof sizes by 40%. That’s huge. It’s bringing them closer to SNARKs in cost while keeping their security edge.
By 2027, we’ll likely see most ZK-Rollups using hybrid architectures. Simple payments? zk-SNARKs. Complex logic? zk-STARKs. The right tool for the job.
Which One Should You Choose?
Ask yourself these questions:
- Do you need low gas costs? Pick zk-SNARKs.
- Are you building for the next 10+ years? Pick zk-STARKs.
- Do you have limited developer time? zk-SNARKs have more docs and tools.
- Are you in a regulated industry? zk-SNARKs are more familiar to auditors.
- Are you handling massive, complex computations? zk-STARKs scale better.
If you’re just starting out and want to launch fast, zk-SNARKs are the safer bet. If you’re building something that needs to survive quantum computing, regulatory scrutiny, and massive scale-go with zk-STARKs.
There’s no universal winner. But there is a winner for your use case.
Can zk-SNARKs be made quantum-resistant?
No, not without a complete redesign. zk-SNARKs rely on elliptic curve cryptography, which quantum computers can break using Shor’s algorithm. While newer variants like Halo 2 remove the trusted setup, they still use ECC. To become quantum-resistant, you’d need to swap the underlying math-effectively turning it into a zk-STARK.
Why are zk-STARK proofs so much larger?
Because they use hash functions and polynomial commitments instead of elliptic curves. Hash functions require more data to prove correctness securely. A zk-SNARK proof is a few hundred bytes because ECC allows compact mathematical representations. zk-STARKs trade size for transparency and quantum resistance. It’s a deliberate design choice, not a flaw.
Is zk-STARK harder to audit?
Actually, it’s easier. Since zk-STARKs have no trusted setup, everything is publicly verifiable. You can check the randomness source, the hash functions used, and the proof logic without relying on any secret data. zk-SNARKs require trust in the setup ceremony, which makes audits harder and riskier.
Can I use zk-SNARKs and zk-STARKs together in the same app?
Yes, and more teams are doing it. Projects like Polygon Miden and Scroll use zk-SNARKs for simple transfers and zk-STARKs for complex smart contract logic. This hybrid approach lets you optimize for cost and scalability at the same time. Think of it like using a bicycle for short trips and a truck for heavy loads.
What’s the biggest mistake developers make when choosing between them?
Choosing based on hype, not requirements. Many jump to zk-STARKs because they’re "the future," but if your app only does simple transfers, you’re paying 5x more in gas for no real benefit. Others stick with zk-SNARKs because they’re familiar, ignoring long-term risks like quantum attacks. The right choice depends on your use case-not what’s trending.

Kathleen Bauer
November 16, 2025 AT 16:49Darren Jones
November 17, 2025 AT 21:26Carol Rice
November 19, 2025 AT 15:08Nidhi Gaur
November 21, 2025 AT 04:48Gaurang Kulkarni
November 21, 2025 AT 21:35jesani amit
November 22, 2025 AT 14:15satish gedam
November 23, 2025 AT 23:10rahul saha
November 25, 2025 AT 13:26Laura Lauwereins
November 27, 2025 AT 12:33Usama Ahmad
November 29, 2025 AT 09:15garrett goggin
November 30, 2025 AT 02:40Nathan Ross
December 1, 2025 AT 01:56Jess Zafarris
December 1, 2025 AT 21:54Peter Rossiter
December 2, 2025 AT 08:12Mike Gransky
December 3, 2025 AT 18:42Kathleen Bauer
December 5, 2025 AT 11:11Ella Davies
December 7, 2025 AT 00:42Jerrad Kyle
December 8, 2025 AT 20:46Usnish Guha
December 10, 2025 AT 03:28Bill Henry
December 10, 2025 AT 10:32