Sybil Attack Cost Calculator
Estimate Attack Feasibility
Calculate the economic cost of launching a Sybil attack on major blockchain networks.
Imagine a voting system where one person can create 1,000 fake identities and control the outcome. That’s exactly what a Sybil attack does to peer-to-peer networks - especially blockchains. It’s not science fiction. It’s a real, proven threat that has already broken smaller networks and could strike again. The name comes from a 1973 book about a woman with 16 personalities, but in tech, it’s about one attacker pretending to be hundreds - or thousands - of users. And it’s one of the biggest reasons some blockchains fail while others survive.
How a Sybil Attack Works
In a true peer-to-peer network, every node is treated as equal. No central server decides who’s trusted. Instead, the network relies on numbers: if 60% of nodes say a transaction is valid, it gets confirmed. That sounds fair - until one person creates 500 fake nodes. Suddenly, they’re not just a participant. They’re the majority.
This isn’t about hacking passwords or stealing keys. It’s about flooding the system with fake identities. Attackers use bots, cheap cloud servers, or even compromised devices to spin up hundreds of nodes. Each one looks real to the network. No one knows they’re controlled by the same person. Once in, they can manipulate voting, block transactions, or even help execute a 51% attack - where the attacker controls enough computing power to rewrite history, reverse payments, or stop new blocks from being added.
Think of it like a town meeting where everyone gets one vote. If you show up with 500 fake IDs, you can pass any law you want. The system doesn’t check if you’re real. It just counts votes.
Why Bitcoin Is Safe - And Smaller Chains Aren’t
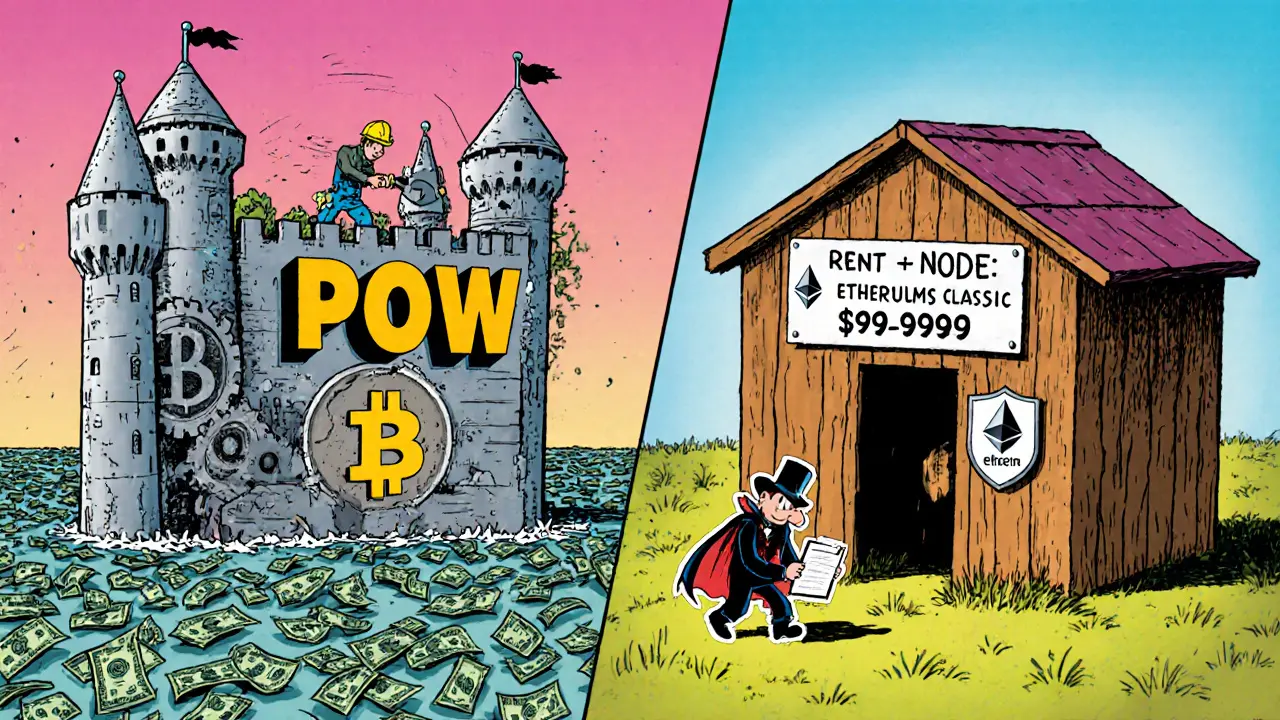
Bitcoin has never suffered a successful Sybil attack. Not once since 2009. Why? Because it doesn’t just count nodes. It counts work.
Bitcoin uses Proof of Work (PoW). To join the network as a validator, you need to solve hard math problems using powerful mining hardware. Each node isn’t just an identity - it’s a $50,000 machine burning through electricity. Creating 51% of the network’s hash power would require over $20 billion in ASIC miners and enough power to match a small country’s usage. The cost is so high, it’s not worth it.
But not every blockchain has that luxury. Smaller networks like Ethereum Classic don’t have the same mining power. In 2019, attackers managed to control more than 50% of its hash rate and pulled off a double-spend attack, stealing over $5 million. Why? Because the cost to launch a Sybil attack was under $100,000. That’s the difference between a fortress and a wooden gate.

How Blockchains Fight Back
There are four main ways networks defend against Sybil attacks - and most use a mix of them.
- Proof of Work (PoW): Requires real computational effort. Fake nodes can’t just appear - they need hardware and energy. Bitcoin and Litecoin use this. It’s expensive, but effective.
- Proof of Stake (PoS): Instead of computing power, you need to lock up real cryptocurrency. Ethereum switched to this in 2022. To become a validator, you must stake 32 ETH. At $3,200 per ETH, that’s over $100,000 just to get started. If you try to fake 51% of the network, you’d need to buy and lock up billions in ETH. That’s not just expensive - it’s self-defeating. If you crash the network, your own stake loses value.
- Social Trust Graphs: These systems map how nodes connect to each other. Real users tend to have stable, long-term connections. Fake nodes show up as random, disconnected spikes. Tools like SybilGuard and SybilRank analyze these patterns to flag suspicious behavior. It’s like spotting a stranger who shows up at every party but knows no one.
- Identity Validation: Some networks ask users to prove who they are - through phone numbers, government IDs, or even social media. But this fights one problem (fake nodes) by creating another: centralization. If you need a government ID to join, you’re no longer truly decentralized. It’s a trade-off between security and freedom.
The Hidden Cost of Security
Adding defenses sounds good - until it pushes users away. Rejolut’s 2024 analysis found that when blockchain platforms added strict identity checks, participation dropped by up to 40%. People don’t want to upload their passport to join a wallet. They want to click, connect, and go.
That’s why the best systems don’t rely on just one layer. Bitcoin doesn’t ask for IDs - it makes attacking too expensive. Ethereum doesn’t just require staking - it uses social trust metrics to detect abnormal node behavior. The most secure networks combine economic barriers with smart detection.
Even then, it’s not perfect. A 2022 CoinDesk survey found that 68% of crypto users had never heard of a Sybil attack. Most people think their wallet is safe because it’s “decentralized.” But decentralization doesn’t mean invincible. It just means the rules are different.
What’s Next? Quantum, DeFi, and the Future of Attacks
As decentralized finance (DeFi) grows, so does the target. The global blockchain security market is expected to hit $33.5 billion by 2028. More money means more attackers. And new threats are on the horizon.
Quantum computing could one day break the cryptography that secures blockchain identities. But IBM’s roadmap says practical quantum attacks are still 10 to 15 years away. That gives networks time to adapt - if they’re smart.
Right now, the biggest risk isn’t quantum. It’s the dozens of new blockchains launching every year with weak consensus models. CipherTrace predicts 37% of new blockchain projects in 2024 will be vulnerable to Sybil attacks. Many will fail quietly. Users won’t even know why their tokens vanished.
The lesson? Not all blockchains are equal. Bitcoin’s security isn’t magic - it’s economics. Ethereum’s shift to PoS wasn’t just about energy savings - it was a shield against attackers. And the networks that survive will be the ones that make attacks too costly, too slow, or too obvious to pull off.
What You Can Do
If you’re using a blockchain - whether for crypto, NFTs, or DeFi - don’t assume it’s safe. Ask: How does this network prevent fake nodes? Is it Proof of Work? Proof of Stake? Does it use reputation systems?
Stick to networks with real economic barriers. Avoid chains that boast high speeds but hide their security model. If no one talks about how they stop Sybil attacks, that’s a red flag.
And if you’re building something? Don’t just count nodes. Make it expensive to fake them. Make it visible when they behave oddly. Make it costly to break the rules. Because in a world without central authority, the only thing stronger than trust is incentive.
What exactly is a Sybil attack?
A Sybil attack happens when a single attacker creates many fake identities (nodes) in a peer-to-peer network to gain control over decisions. In blockchain, this can let them manipulate voting, block transactions, or enable double-spending by pretending to be a majority of users.
Can a Sybil attack happen on Bitcoin?
No, Bitcoin has never suffered a successful Sybil attack. Its Proof of Work system requires massive computing power and energy to create each valid node. Controlling 51% of Bitcoin’s network would cost over $20 billion in hardware and electricity, making it economically impossible.
How does Proof of Stake stop Sybil attacks?
Proof of Stake ties network participation to real cryptocurrency holdings. To become a validator on Ethereum, you must lock up 32 ETH - worth over $100,000. To launch a Sybil attack, you’d need to buy and stake billions in ETH. If you try to crash the network, your own stake loses value, making the attack self-defeating.
Why did Ethereum Classic get hacked in 2019?
Ethereum Classic had a much smaller mining network than Bitcoin or Ethereum. Attackers were able to rent enough hash power for under $100,000 to control over 50% of the network. This let them reverse transactions and steal funds - proving that small blockchains are vulnerable when they lack economic security.
Are identity checks a good way to prevent Sybil attacks?
They can help, but they come at a cost. Requiring government IDs or phone numbers makes it harder to create fake nodes - but it also removes decentralization. If you need to prove who you are to join, you’re no longer truly peer-to-peer. Many experts say economic barriers (like PoW or PoS) are better because they don’t sacrifice core principles.
What’s the best defense against Sybil attacks?
The strongest defense combines multiple layers: economic barriers (Proof of Work or Proof of Stake) to make attacks expensive, social trust graphs to detect abnormal node behavior, and limited identity checks only where necessary. No single method is perfect - but together, they make Sybil attacks too costly, too slow, and too risky to attempt.


Adrian Bailey
November 11, 2025 AT 20:18man i just read this whole thing and i’m lowkey shook. i thought crypto was just about buying shitcoins and hoping they moon, but this sybil stuff? it’s like someone hacked the democracy of the internet. and the part about bitcoin being safe because it’s too expensive to attack? that’s wild. i mean, who even has 20 billion to throw at a blockchain? not me, not my uncle bob who thinks dogecoin is the future. also, typo: 'ASIC miners' not 'ASCI' lol
Wayne Dave Arceo
November 13, 2025 AT 13:05Let me correct the record: the claim that Bitcoin is immune to Sybil attacks is misleading. It’s not immune-it’s economically infeasible. The distinction matters. Sybil resistance ≠ Sybil immunity. And no, your ‘$20 billion’ figure is outdated. ASICs have improved efficiency. The real barrier is not cost-it’s capital concentration. The 1% of miners control 90% of hash rate. That’s not decentralization. That’s oligarchy with a blockchain sticker.
Laura Hall
November 14, 2025 AT 18:03This was such a thoughtful breakdown. I especially appreciated how you explained the trade-offs between security and decentralization. It’s easy to assume more security always equals better, but when users have to upload their passport just to send $5, you start to wonder what you’re even protecting. The social trust graphs idea feels like the most elegant solution-like recognizing a stranger at a family reunion who doesn’t know anyone’s name.
Rebecca Saffle
November 16, 2025 AT 13:03So let me get this straight-Bitcoin is ‘secure’ because only billionaires can afford to break it? That’s not security, that’s elitism. And you call that freedom? What a joke. Meanwhile, I’m trying to send crypto to my cousin in Puerto Rico and the fees are $12. Who benefits here? Not the people. The system is rigged.
Arthur Crone
November 18, 2025 AT 10:05Proof of Stake is a scam. You’re locking up tokens you already own to become a validator? That’s not security, that’s rent-seeking. PoW at least requires real work. PoS just rewards the rich. Ethereum’s shift was a surrender to Wall Street. And don’t get me started on ‘social trust graphs’-that’s just surveillance with a crypto label.
Michael Heitzer
November 20, 2025 AT 05:04Guys, think bigger. The real question isn’t how to stop Sybil attacks-it’s why we’re still building networks that need to stop them. What if we stopped treating nodes like voters and started treating them like collaborators? Imagine a system where reputation is earned over time, not bought with ETH or ASICs. Where your contribution-code, support, translation-builds your weight. That’s not just secure. That’s human.
Ashley Mona
November 20, 2025 AT 13:39omg this is so fire 🔥 i literally cried when i read the part about ethereum classic. like, imagine spending $100k to steal $5M? that’s not hacking, that’s a bad business plan 😂 but also… what if we just made every node have to do a tiny 5-second video selfie verifying their face? like, just once. then boom. no more bots. easy. why hasn’t this been done??
Johanna Lesmayoux lamare
November 22, 2025 AT 00:30Interesting. But what about mobile nodes? Most people access crypto via phones now. Could a Sybil attack happen through compromised Android devices? Just wondering.
tom west
November 23, 2025 AT 17:38Let’s be honest-90% of these ‘blockchain projects’ are vaporware. They don’t even understand the basics of consensus. The fact that anyone still thinks ‘fast transactions’ matter more than security is why this industry is a dumpster fire. PoW is clunky. PoS is centralized. Identity checks are authoritarian. We’re choosing the least bad option while pretending we’re building utopia. Wake up.
dhirendra pratap singh
November 24, 2025 AT 13:26THIS IS WHY I HATE AMERICA. You guys think money solves everything. You think if you throw enough ETH at a problem, it goes away. But in India, we know real security comes from community. We don’t need $100k staking-we need trust. My uncle runs a local crypto group. No bots. No hacks. Just 12 people who meet every Sunday. They know each other’s kids’ names. That’s real decentralization. You all are lost.
Rachel Everson
November 25, 2025 AT 01:47Just wanted to say-this is one of the clearest explanations I’ve read. I’m a teacher and I used this to explain blockchain security to my high school class. They actually got it. The town meeting analogy? Perfect. And the part about participation dropping 40% when you add ID checks? That’s so real. People don’t want to be vetted. They want to participate. We need to design for that.
Edward Phuakwatana
November 26, 2025 AT 13:19Bro, we’re missing the forest for the trees. Sybil attacks are just the symptom. The disease is the myth of permissionless innovation. You can’t have true decentralization without economic friction. But you also can’t have mass adoption without UX. The future isn’t PoW or PoS-it’s hybrid consensus layers with dynamic reputation scoring + zero-knowledge identity proofs. We’re already seeing prototypes in zkSync and Polygon CDK. The tech is here. The narrative just hasn’t caught up.
Suhail Kashmiri
November 27, 2025 AT 15:23you think bitcoin is safe? lol. i saw a guy on reddit say he mined 5000 btc in 2010. how? he had 3000 rigs in his basement. now he’s in jail. so who really controls the network? the guy with the biggest basement. not god. not the code. just the guy with the most electricity. and now he’s in the senate.
ty ty
November 28, 2025 AT 02:37Wow. So the solution to fake identities is… more money? That’s genius. Next you’ll tell me the way to stop spam is to charge $100 per email. Brilliant. I’m sure the 14-year-old in Bangladesh who wants to send 5 cents to his mom is thrilled.
Debraj Dutta
November 28, 2025 AT 17:24Very well written. I work in telecom in India and we see similar patterns in SIM fraud. One person registers 200 SIMs with fake IDs. The telecom company uses device fingerprinting and behavioral analysis-similar to social trust graphs. The solution is never one tool. It’s layers. And patience. We’ve been fighting this for 15 years. Blockchain is just starting.
Kristin LeGard
November 30, 2025 AT 08:08So you’re saying Bitcoin is safe because only rich people can afford to attack it? That’s not security. That’s fascism. And you call that freedom? I’m sick of this techno-libertarian nonsense. The system is broken. The rich get richer. The poor get locked out. And you’re celebrating it like it’s a feature.
Joanne Lee
December 1, 2025 AT 06:18Thank you for this comprehensive overview. I found the comparison between economic barriers and identity validation particularly illuminating. It’s a delicate balance-one that requires both technical rigor and ethical consideration. The fact that 68% of users are unaware of Sybil attacks underscores a critical gap in user education. Perhaps the next step isn’t just better protocols, but better literacy.
BRYAN CHAGUA
December 3, 2025 AT 04:28This is one of those posts that makes you pause. We’re building a new financial system, but we’re still thinking like old-world gatekeepers. Maybe the answer isn’t more barriers-but more transparency. What if every node had to publish a public log of its activity? Not personal data-just behavior patterns? We could build trust through openness, not exclusion. Just a thought.